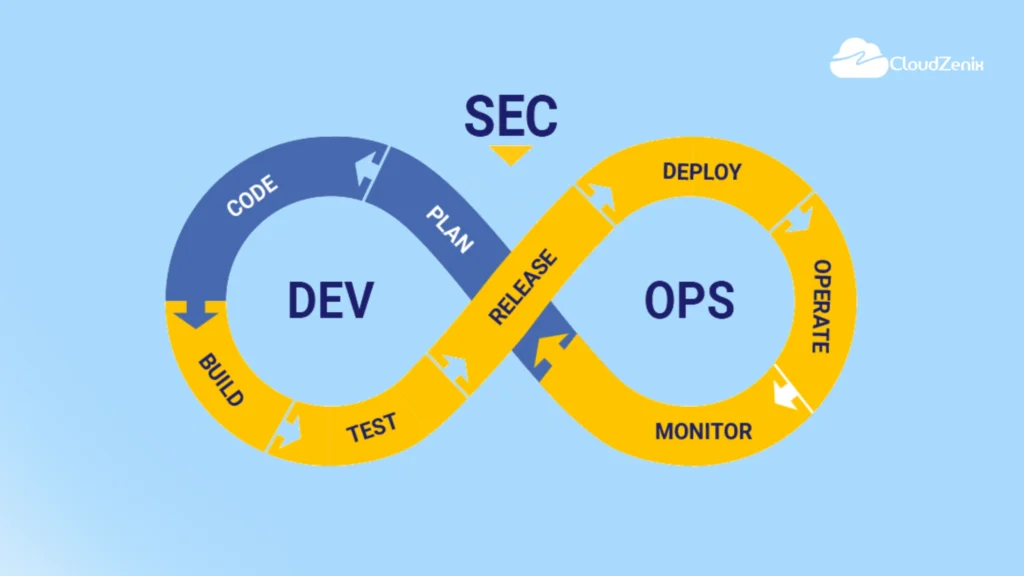
Introduction:
By integrating security throughout the whole software development lifecycle, DevSecOps—a combination of development, security, and operations—revolutionizes the field. The process of developing, packaging, and distributing apps changes dramatically in this era of automated application delivery.
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tool integration become critical to addressing security vulnerabilities in a typical CI/CD workflow.
DevSecOps:
DevSecOps—short for development, security, and operations—automates the integration of security at every phase of the software development lifecycle.
Nowadays, Building software applications has seen a big transformation when it comes to automating the delivery applications – The process of compiling building, and packaging the applications from source code into executable binaries, will deploy these binaries into live environments to be accessed by users.
To solve the security vulnerabilities in a standard CI/CD pipeline incorporating SAST and DAST tools.
| S.NO. |
Static Application Security Testing | Dynamic Application Security Testing |
| 1. | SAST is a type of White Box security testing. | DAST is a type of Black Box security testing. |
| 2. | In SAST, the application is tested from the inside out. | In DAST, the application is tested from outside in. |
| 3. | This type of testing is a developer’s approach to testing. | This type of testing is a hacker’s approach to testing. |
| 4. | No deployed application is required for Static Application Security Testing. | A running application is required for Dynamic Application Security Testing. |
| 5. | SAST can not discover issues related to run time and environment. | DAST can discover issues related to run time and environment. |
| 6. | SAST testing requires source code to perform testing operations. | DAST testing does not require source code to perform testing operations. |
| 7. | This testing is performed in the early stages of the Software Development Life Cycle (SDLC). | This testing is performed at the end of the Software Development Life Cycle (SDLC). |
DevSecOps pipeline achieved through GitLab-CI:
GitLab-CI:
- In place of “Initializer” use GitLab-CI as “continuous integration and continuous delivery CI/CD” which can help in building, packaging, and deploying applications in terms of the automation process.
- The overall architecture of the GitLab CI/CD is like a “master-slave” based architecture. In practical terms, this means that the GitLab Server will act as a master, who will read and interpret the “.gitlab-ci.yml” file, which is where the pipeline will be defined.
- Then, it will assign each of the jobs to a slave, which is called the GitLab Runners.
SonarQube: Source-Code Analysis
- SonarQube is an open-source source-code analysis tool developed by SonarSource that performs static analysis of source code “to detect bugs, code smells, and security vulnerabilities”
- Usage of this tool offers many advantages such as: using it is significantly faster than manually reviewing the code; since it does not require any live deployment of the application, it can be performed earlier in the software’s life-cycle – even without a deployment-ready version of the application.
Docker:
- Used containerization platform for developing, deploying, and managing applications in lightweight virtualized.
- After compiling the source code, a Binary artifact will be created, using this docker images will be built for isolating applications from one another.
- Further applications will be run as a container.
Clair: (Container Security)
- Clair scans docker images by doing static analysis, which means it analyzes images without a need to run their docker container.
- Clair is composed of 2 components:
1. Clair
- REST API server CVE.
- Updater which takes care of updating.
- Database of vulnerabilitiesList of CVE data sources
2.PostgreSQL 9.4+
- Storage of vulnerabilities database and results of analysis of uploaded docker image layers
Gitleaks: (Secrets Scanning)
- Secrets Scanning is the name given to a scan run by the application’s source code against a list of various regex patterns that are often associated with content that should be secret and/or not hard-wired directly in the application’s source code, such as passwords, API Keys, personal information, etc.
- Gitleaks is an open-source SAST tool for scanning secrets in git source-code repositories. It works by performing regex analysis based on a set of rules that can be customized in a TOML file, also tool supports JSON and CSV reporting
OWASP: (Dependency Scanning)
- Dependency Scanning is the name given to a type of SAST that consists in analyzing a project’s library dependencies.
- And verify if any of them have known vulnerabilities associated, by checking the library and respective version against a database of publicly known vulnerabilities (CVEs).
- It works by gathering information about the dependencies using Analyzers.
- For example, the JarAnalyzer (part of the Dependency-Check engine) will collect information from the Manifest, pom.xml, and the package names in the JAR files, and then check them for known vulnerabilities.
Zed Attack Proxy: (DAST)
- As opposed to SAST, which does not require a deployment of the application.
- The OWASP Zed Attack Proxy, (ZAP) is a Web-Application Security tool also developed under the OWASP Foundation, which aims to help security professionals automatically find security vulnerabilities in web applications.
- ZAP creates a proxy server and makes your website traffic pass through that server.
- It comprises auto scanners that help you intercept the vulnerabilities in your website.
DefectDojo: (Vulnerability Management)
- DefectDojo is an open-source vulnerability management tool, also developed as a part of the OWASP Project.
- The goal of the tool is to help organizations manage their Application Security programs by providing a platform to aggregate all the information about vulnerabilities
- The application natively supports integration with over 20 other security tools
Conclusion:
Within the framework of DevSecOps, a robust security practice is made possible by a well-orchestrated pipeline that is attained by GitLab-CI. SonarQube, Docker, Clair, Gitleaks, OWASP, and DefectDojo are just a few of the tools that work together to protect apps from possible attacks.
Organizations can meet the ever-changing demands of the modern tech world by implementing these solutions, which guarantee a software development process that is secure, effective, and streamlined.